Terms
  |
Penetration Testing
Penetration testing (also called pen testing) is the practice of testing a computer system, network, or Web application to find vulnerabilities that an attacker could exploit. |
  |
Personal Area Network
A computer network used for data transmission among digital devices. Interconnected devices are operating in the range of a single person, typically 10 meters. PANS are mostly or exclusively wireless, making the term basically indistinguishable from Wireless PANs (WPAN). |
  |
Personally Identifiable Information
Personally identifiable information (PII), or Sensitive Personal Information (SPI), as used in US privacy law and information security, is information that can be used on its own or with other information to identify, contact, or locate a single person, or to identify an individual in context. |
  |
Personal Protection Drone
A type of drone, or drone swarm, dedicated to an individual’s security. PPDs are non-lethal and may be primarily used to record an encounter or raise an alarm. |
  |
Pervasive Computing
Pervasive computing (also called ubiquitous computing) is the growing trend towards embedding microprocessors in everyday objects so they can communicate information. Pervasive computing devices are completely connected and constantly available. |
  |
Platform as a Service
Platform as a service (PaaS) is a category of cloud computing services that provides a platform allowing customers to develop, run, and manage web applications without the complexity of building and maintaining the infrastructure typically associated with developing and launching an app. |
 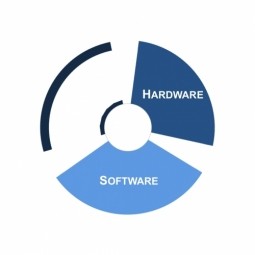 |
Point-to-Point Tunneling Protocol
Point-to-Point Tunneling Protocol (PPTP) is a protocol that allows corporations to extend their own corporate network through private "tunnels" over the public Internet. |
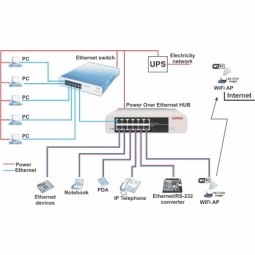  |
Power over Ethernet
Power over Ethernet (PoE) describes any of several standardized or ad-hoc systems that pass electrical power along with data on Ethernet cabling. This allows a single cable to provide both data connection and electrical power to devices such as wireless access points or IP cameras. |
  |
Power over WiFi
A technology that can convert the signals sent by wireless routers into DC (direct current). WiFi hotspots and routers are programmed under PoWiFi to broadcast noise when a channel is not being used to send data, thus providing a continuous stream of low-power signals that can be harvested. |
  |
Pre-Boot Authentication
Pre-Boot Authentication (PBA) or Power-On Authentication (POA) serves as an extension of the BIOS or boot firmware and guarantees a secure, tamper-proof environment external to the operating system as a trusted authentication layer. |
  |
Preboot Execution Environment
A Preboot Execution Environment (PXE) -enabled device can be shut down or restarted via a network connection, allowing for power-hungry devices to be managed remotely. It is the ability to manage power over a network connection |
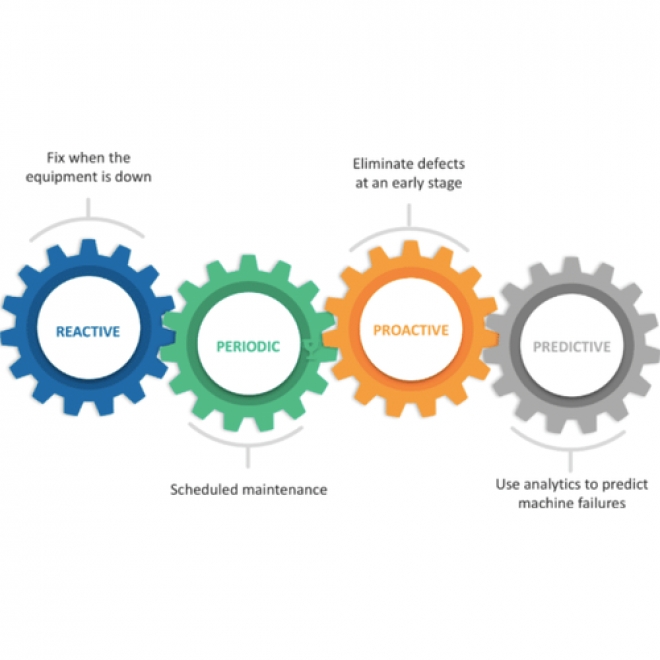  |
Predictive Maintenance
Predictive maintenance is a technique to predict the future failure point of a machine component, so that the component can be replaced, based on a plan, just before it fails. Thus, equipment downtime is minimized, and the component lifetime is maximized. |
  |
Pressure Sensor
A pressure sensor measures pressure, typically of gases or liquids. The pressure is an expression of the force required to stop a fluid from expanding and is usually stated in terms of force per unit area. A pressure sensor usually acts as a transducer. |
|
Preventive Maintenance
Preventive maintenance is regularly performed on a piece of equipment to reduce the likelihood of failure. Preventive maintenance ensures that anything of value to your organization receives consistent maintenance to avoid unexpected breakdowns and costly disruptions. |
|
  |
Privacy by Design
Privacy by Design is an approach to systems engineering, which takes privacy into account throughout the whole engineering process. The concept is an example of a value-sensitive design. |
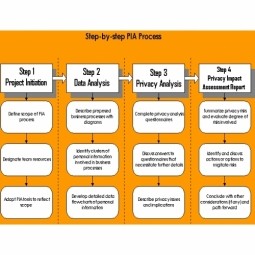  |
Privacy Impact Assessment
A privacy impact assessment (PIA) is a tool for identifying and assessing privacy risks throughout the development life cycle of a program or system. A PIA should identify: Whether the information being collected complies with privacy-related legal and regulatory compliance requirements. |
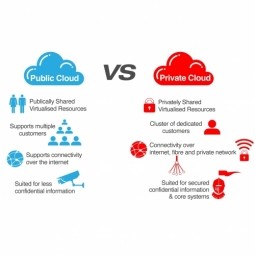  |
Private Cloud
A private cloud provides services with cloud characteristics but only within a single organization, for example, one company. As a result, the private cloud is best for businesses with dynamic or unpredictable computing needs that require direct control over their environments. |
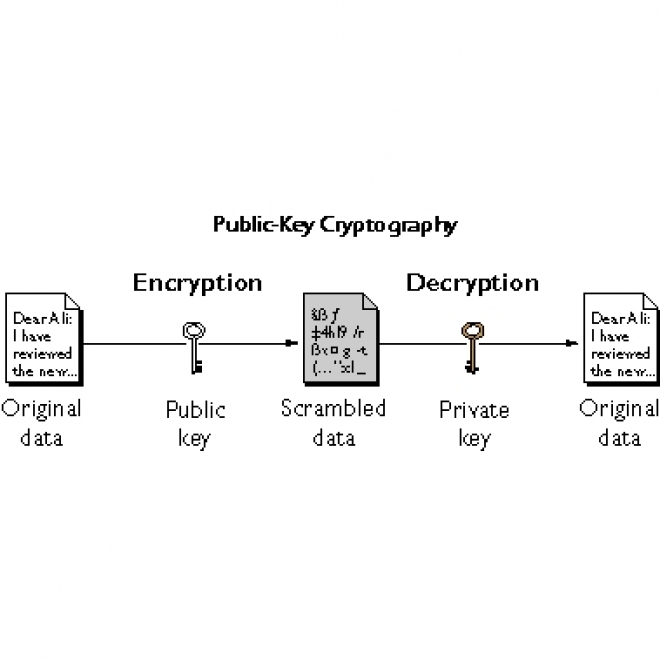 |
Private Key
The private key is paired with a public key to set off algorithms for transaction encryption and decryption. It is created as part of public-key cryptography during asymmetric-key encryption and used to decrypt and transform a message into a readable format. |
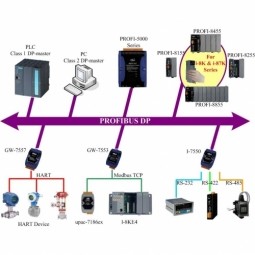  |
Process Field Bus
Process Field Bus (PROFIBUS) is a standard for fieldbus communication in automation technology and was first promoted in 1989 by BMBF (German department of education and research) and then used by Siemens. |
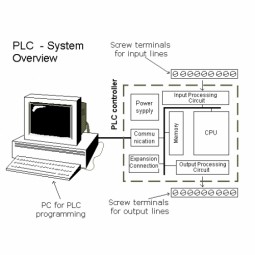  |
Programmable Logic Controller
A programmable logic controller (PLC) is a digital computer used for automation of typically industrial electromechanical processes, such as control of machinery on factory assembly lines, amusement rides, or light fixtures. |
 |
Proof of Stake
A consensus distribution algorithm that rewards earnings based on the number of coins you hold. This consensus algorithm is used to secure the network and confirm transactions, just like proof of work. |
_1.jpg) |
Proof of Work
A consensus distribution algorithm that requires computational power in the form of mining data blocks. This measure is used to deter denial of service attacks and other service abuses. |
  |
Proxy Server
In computer networks, a proxy server is a server (a computer system or an application) that acts as an intermediary for requests from clients seeking resources from other servers. |
 |
Public Address
Public Address is a string of alphanumeric characters that are uniquely tied to a specific private address. Similar to an email address to send/receive emails, the public address is used to send/receive cryptocurrencies. |
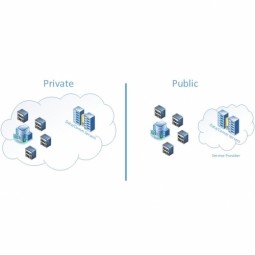  |
Public Cloud
The public cloud is defined as computing services offered by third-party providers over the public Internet. Resources vary by provider but may include storage capabilities, applications or virtual machines. |
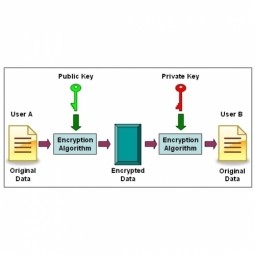  |
Public Key Infrastructure
A public key infrastructure (PKI) supports the distribution and identification of public encryption keys, enabling users and computers to both securely exchange data over networks such as the Internet and verify the identity of the other party. |
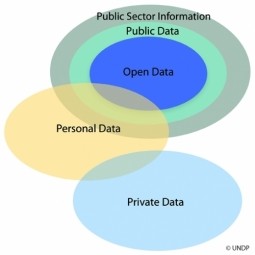  |
Public Sector Information
Public sector information (PSI) is information produced by central and local government or any other public body. The purpose of a PKI is to facilitate the secure electronic transfer of information for a range of network activities such as e-commerce, internet banking and confidential email. |
  |
Quality of Service
Quality of service (QoS) is the overall performance of a telephony or computer network, particularly the performance seen by the users of the network. |
  |
Quantified Self
Quantified self is a movement that incorporates technology such as sensors and wearables to monitor humans activities, such as moods, habits, diet, and drug combinations. This data is then used to improve a person’s lifestyle and state of mind. |
  |
Quantum Sensor
A quantum sensor is a device that exploits quantum correlations, such as quantum entanglement, to achieve a sensitivity or resolution that is better than to use only classical systems. |
